Email authentication and its importance in email marketing (4/8)
Module 4 - Authenticate your corporate email
Email authentication is your greatest defence as a sender against harmful email address spoofing or phishing attacks. However, authentication is not easy and can be very technical. So let's (try to) break it down in simple terms.
So in this lesson we will discover:
- Why email authentication is a critical component of any email marketing program
- The 3 basic email authentication methods (SPF, DKIM and DMARC)
- The most recent entry in the email authentication area (BIMI)
- The pros and cons of each method and how they work together to enhance your email program and strengthen your deliverability
Email authentication

Email authentication is an important process that requires collaboration between your email service provider (ESP), your IT department (or whoever else manages your email infrastructure) and possibly your company's marketing department. Authentication is critical because it helps to confirm and verify the identity of the email sender. Following email authentication best practices helps protect your business from third parties who want to hack or spoof your email address. It also helps to increase your recipients' trust in your brand by preventing unwanted and dangerous emails in their inbox.
Email authentication is not easy and can be very technical.
So, let's take a general look at the three different email authentication processes that, when configured correctly, will enhance deliverability.
We will discuss:
- Shipper's policy box or SPF
- DomainKeys Identified Mail or DKIM
- Reporting and message authentication compliance based on domain or DMARC
These are the three main methods of authentication that work to confirm the identity of the sender during the email transfer process.
We will also discuss the most new way of authentication, BIMI and how it relates to the three email authentication processes.
SPF
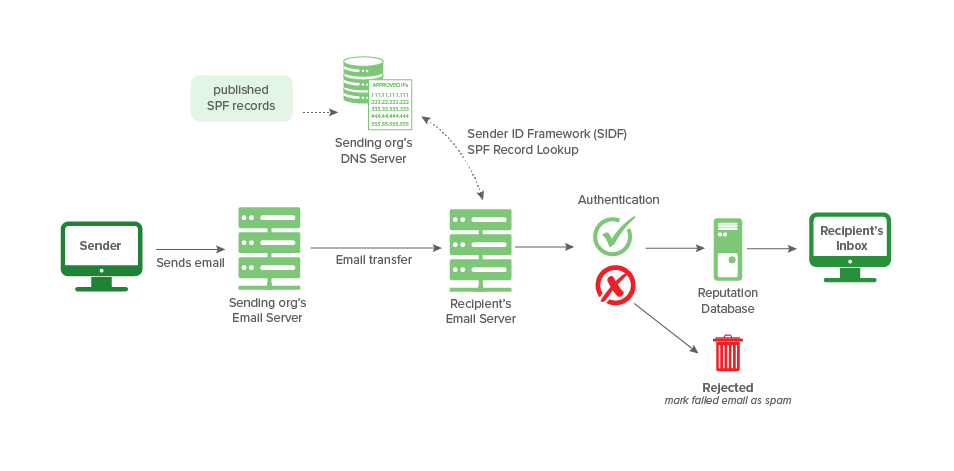
SPF is the first email authentication method you need to put in place as a sender. Yes, SPF is said and has nothing to do with sun protection, but it protects you as it allows your company as your domain owner to say which IPs can send messages email on your behalf. Instead, it also tells the email servers that mail coming from an IP not listed in your SPF record is not really coming from your company and should be rejected.
The SPF application requires you to set up a DNS TXT record containing the IPs that are allowed to send emails on behalf of your domain. For example, if the IP that your company uses to send marketing emails is: 50.201.69.200, then the DNS TXT record would look like this: v=spf1 ip4:50.201.69.200 -all
If you have multiple sending IP addresses, you can indicate all of them in your SPF registration.
SPF is checked during the Simple Mail Transfer Protocol (SMTP) process and returns a result. Here are some possible results:
- None, there is no SPF record to search or the SPF search returned no results.
- Neutral, which means that information is missing. This will be treated as no result.
- Come in, which means it was verified by the email provider.
- Failure, which means that the IP address is not authorized to send mail. The mail and will be sent!
- Partial failure, which means that the IP address may or may not be authorized for sending from the domain. These emails will not be blocked - they are usually sent to subscribers' spam folders and flagged as suspicious.
SPF authentication sounds great, right? Well, it has pros and cons.
The advantages of SPF is:
- It uses a simple format for the initial setup.
- The SPF is easily added to the DNS zone as a small TXT record.
- Maintenance is easy if you have the access, tools and understanding to change or maintain DNS.
The disadvantages of SPF is:
- The format can become complex quickly, especially when adding "include" instructions for multiple IPs.
- SPF can be complex as far as updating it to accommodate many domains.
- Since it is easy to configure, there is nothing to prevent unwanted or malicious users from having perfect SPF files.
SFP is only valid for SMTP chat - does not help to authenticate the email message itself.
SPF is a great first step, but is not enough to fully secure your program.
This brings us to DKIM.
DKIM
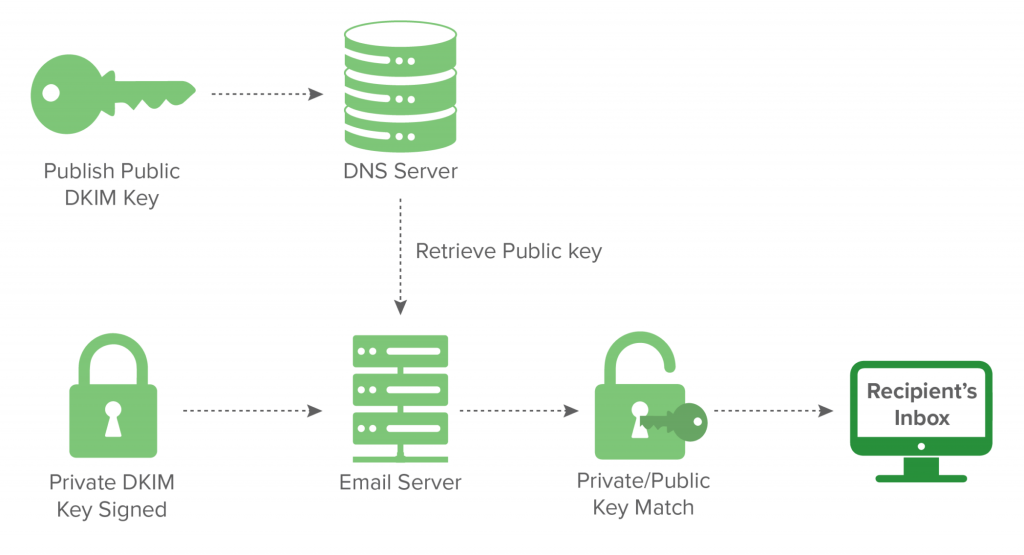
DKIM was designed to fill some of the gaps that SPF authentication cannot fill. In addition, without DKIM registration, you will not be able to take full advantage of DMARC, a more rigorous standard that we will cover below.
DKIM helps organisations take responsibility for sending messages in a way that is verifiable by electronic mailbox providers. To do this, cryptographic authentication must be in place. The creation of the envelope and associated keys requires some technical knowledge.
So let's go step by step. As an email message is sent, the message transfer agent (MTA) adds a unique DKIM signature header containing the signature of the message and the information used to create the signature.
After receiving the email, the MTA uses the public key from the DNS TXT record and matches it with the values in the DKIM signature header to determine if the message signature is valid or if the message was changed in transit.
This returns a result.
Possible outcomes include:
- None, which means that no DKIM registration has been set up.
- Come in, which means that the verification check of the mailbox provider has passed.
And...
- Failure, which means that there is a DKIM signature, but there was an error that caused the verification to fail.
This result may mean that the message was modified during delivery or that there was a significant configuration error in the DKIM record on the sender's server.
As with the SPF, the DKIM record includes many parts including the signing algorithm, the dialer, the domain used with the dialer record to identify the public key, and more. Again, we only cover the main points here.
Next, let's talk about the advantages and disadvantages of DKIM.
The advantages of DKIM is:
- When using large mailing lists, it can help reduce the restriction applied by large Internet service providers.
- It can reduce the chance of your messages being filtered as spam when sending to a large list from a domain.
- Unlike SPF, the DKIM signature accompanies the message even when the email is forwarded, as long as the forwarding user does not change the message headers or the body of the message.
The disadvantages of DKIM include the fact that:
- DKIM can be difficult to implement.
- It does not tell recipients to take any particular action.
- Does not prevent "header" sector forgery.
- It does not prevent forgery of the brand name.
- And DKIM is not visible to the non-technical end user.
As with SPF, DKIM alone is not enough to keep those pesky phishers and spoofers away. So, let's get to the third authentication protocol.
DMARC
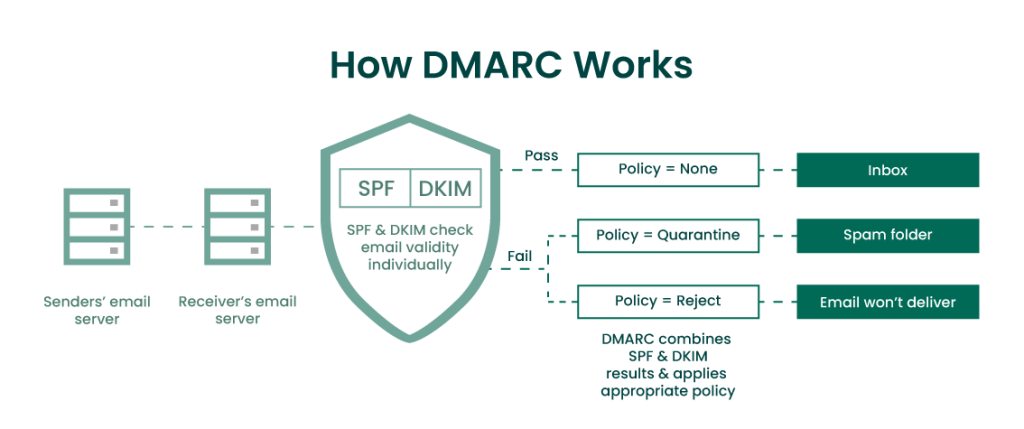
DMARC is an email authentication method that helps to detect phishing attempts. Retrieved from three main functions:
- Authenticates email messages for email sending domains.
- It tells mailbox providers what to do if their email fails authentication.
- Depending on the policy you set, your messages can be sent to a spam folder or rejected altogether, protecting consumers from exposure to attacks.
DMARC also includes action planning and security strategy. The security policy you define may require the recipient to send aggregate reports to the sender. Obtaining information about potential threats helps senders identify malicious emails against their customers and better protect the brand from phishing and forgery.
DMARC was created by a consortium of companies that includes Validity. As with SPF and DKIM, setting up DMARC requires adding the security policy to a DNS TXT record that specifies what to do with an email message that fails one or more checks, including DKIM, SPF, and domain stacking. This policy also specifies the percentage of messages to be checked against the policy and how to report any failures.
Both SPF and DKIM have either:
- Relaxed setting, where only the original domain from the mail from the address must match the original domain of the friendly from the address.
- Strict setting, where the field from the mailing address from must match exactly.
- For both SPF and DKIM, if you do not specify a setting type, then the loose setting is applied.
Of course, DMARC also has positives and negatives.
The advantages of DMARC is:
- The idea is simple.
- DMARC provides an extra layer of security for the highest level of authentication currently available.
- DMARC provides you with the ability to set security policies to determine what to do with e-mail messages that do not pass this authentication check. This helps give you more control over the level of protection you provide to your recipients.
- DMARC is a DNS TXT record that can be easily defined by anyone with access to the email infrastructure. As senders gain more experience, they can "tighten the ropes" and update its security policy and set stricter criteria.
The disadvantages of DMARC include:
- Execution can be difficult, as different companies may have multiple email domains and their emailing practices may not always be aligned. As a result, they should all be aligned with a common policy.
- DMARC reports are not easy to read on their own, the volume of reports can be huge and one must be able and willing to understand and interpret the reports.
- The cost of failure is high, as undeliverable email has a real cost to businesses. If DMARC is implemented incorrectly, legitimate mail can end up in the trash (not even in the junk, it just won't be sent/delivered).
BIMI
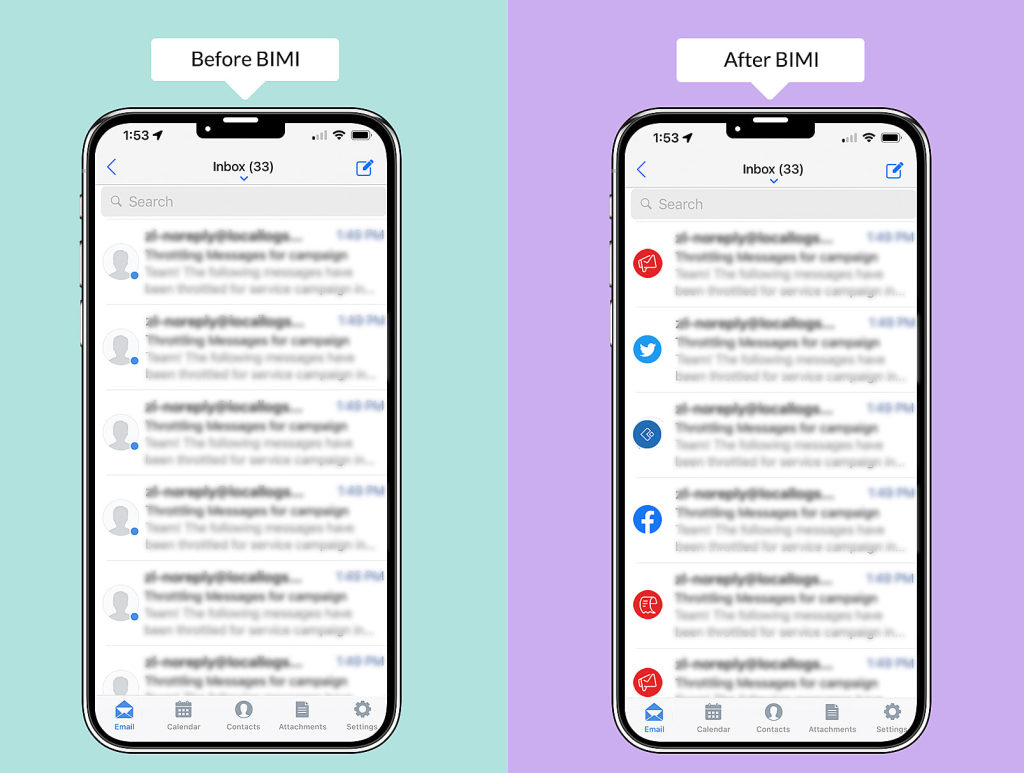
Last but not least, we have BIMI.
BIMI is the most recent way of email authentication. Although BIMI itself is not a means of authentication, it aims to adopt strong sender authentication for the entire email ecosystem, requiring the use of DMARC. Major mailbox providers such as Google, Yahoo!, etc., now support BIMI.
BIMI works by allowing the display of a verified company logo next to the email of the sender in the inbox. This visually reinforces the identity of the sender's name and provides assurance to the recipient that the email can be trusted. It also helps senders stand out as the inbox fills up more.
A sender must implement the recommended authentication protocols to use BIMI. See? All these protocols are interconnected. The use of BIMI requires a strict DMARC policy, which in return requires the correct configuration of SPF and DKIM DNS TXT records.
Let's discuss the pros and cons.
Advantages of BIMI:
- Helps secure an email program by requiring email authentication.
- Improves brand presence in busy inboxes.
- It inspires a feeling of trust with your recipients, as they see your logo and know immediately who is sending the message.
Disadvantages of BIMI:
- Correct SPF, DKIM and DMARC settings take time.
- Companies must have a certified and approved brand logo before implementing BIMI.
- All email authentication methods and BIMI work together to ensure that all email transfer systems and your recipients know that you are the sender!
Oof. That was enough, wasn't it? I hope you are still with me and if you are indeed, congratulations as the article was quite technical.
So you are one step closer to becoming a master of tradition. Start applying what you have read to your own business and don't forget to read the next section on the Design Newsletter.



